The technology boom in logistics has had enormous benefits for businesses. Companies keen to ensure the safety of their cargo and improve the efficiency of their routes can now track shipments. Clients can see when their delivery will arrive and engineers can use mobile devices to control industrial processes. New technology will transform both business and society.
Kirsten Williams, Allan & Associates James Pothecary, Allan & Associates
However, with new technology comes a greater risk of sophisticated cyberattacks, especially against transporters in supply chains and programmes that monitor processes. Today, hackers can reveal and co-opt tracking technology; port systems can be hacked to move or even remove containers; and entire control systems can be altered or taken offline. This poses a huge risk for logistics companies dealing in process engineering.
Not-so-smart technology
Smart devices connected to digital networks tend to be insecure and unguarded. This leaves commercial and personal networks highly vulnerable to infiltration. On 5 August 2016, security researchers successfully hacked a Nest smart thermostat. Criminals replicating this feat could monitor when homeowners were away from the property.
This incident is deeply concerning not just because it shows how devices can be rendered useless or otherwise manipulated by malicious hackers, but how such smart technology can be used as an entry point to a company or individual's entire online network.
Such hacks of thermostats and other “smart” control devices have the potential to cause ruinous levels of damage to a business. In December 2014, cybercriminals hacked into the emails of a German steel mill, stealing login information and using it to access the plant’s production systems.
It forced the emergency shutdown of a blast furnace and caused major damage. Researchers believe that cyberattacks which cause physical damage are far more common than reports suggest, since companies are unwilling to publicise the cases.
Attacks on control systems, when they cause physical damage, also make companies vulnerable to breaches of compliance standards. In a worst case scenario, a business could be exposed to massive litigation. Security researchers were even able to hack patient monitors in U.S. hospitals in February 2016, allowing them to gain access to confidential data and tamper with vital information.
Were hackers to do the same, this could be even more damaging than their current approach, which is to lock hospitals out of their patient files by encrypting them until a ransom is paid, usually in the virtual currency Bitcoin. One anti-hacking consultancy estimates that there has been a fivefold increase in cyber ransom attacks in Europe in the last year, from 131,000 to 718,000.
Cyber-criminals have combined with pirates to stage audacious attacks. In 2016, communications company Verizon reported that the vessels of one of its clients, a global shipping conglomerate, were repeatedly attacked by pirates: they would board the ship, contain the crew in a particular area and then leave a short time later, after stealing from particular containers that they identified by their barcodes.
Verizon discovered that the pirates had hacked into the company’s online content management system and downloaded the ships’ cargo manifests.
Sophisticated hacks mean that logistics companies risk becoming unwittingly involved in serious crime themselves. Workers at the Belgian port of Antwerp had no idea that their location system had been hacked until entire containers started to disappear in 2013.
It later transpired that a Dutch organised crime syndicate had been hiding drugs, guns and cash in legal shipments over a two-year period. Hackers had changed driver credentials and schedules so organised crime gangs could arrange for their own drivers to smuggle the illicit goods out of the port in accredited lorries.
One lorry driver with no links to the gang accidentally drove off in a container filled with cocaine and narrowly escaped being shot dead.
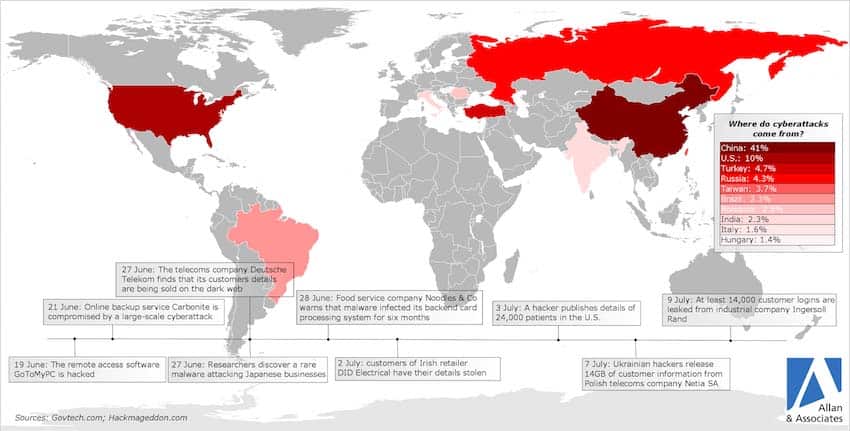
The dystopian nightmare: just a dream
A primary concern amongst the general public and commercial entities, particularly those engaged in sophisticated and sensitive industries, is the threat posed by foreign hostile governments.
However, as it currently stands, the realistic threat this poses to commercial entities is low. Government cyberattacks are primarily (although not exclusively) focused on hostile states.
These occasionally take the form of the classic nightmare scenario – the U.S.-Israeli Stuxnet virus that was used against Iranian nuclear digital infrastructure is one example. The Lithuanian and Estonian parliaments, and the Ukrainian power grid, all accuse Russia of employing hackers against them.
The state-owned Islamic Republic of Iran Shipping Lines (IRISL) was targeted by hackers who stole information and crashed its tracking system in August 2011.
The head of the IRISL said that the extent of the attack suggested it was being backed by ‘powerful sources’. The shipping line has long been affected by Western sanctions after being accused of transporting weapons, an accusation it denies.
Yet such efforts are politically focused, and rarely target commercial interests. In the case of Iran in particular, the country has powerful enemies and is thus a special case.
For the moment, businesses should not be overly concerned by state cyber-attacks. As it currently stands, such attacks, when they do occur, are limited to denial of service (DDoS) or distributed denial of service strikes (DDoS).
These attacks flood company networks with traffic, causing them to crash, and in the case of DDoS, can be orchestrated by hundreds of thousands of computers. While superficially alarming, they do not pose a substantial long-term threat to commercial entities.
Conclusion
The increasing reliance of companies on automated online systems simultaneously raises the security risk facing the company from hostile outside forces. Conversely, failure to take full advantage of such systems will leave a company at a competitive disadvantage.
In order to find a compromise between these two positions, companies must invest in cyber security at the same time as they move more and more elements of their business online.
The admittedly substantial costs of investment in cyber defence must be regarded by all businesses as an essential and non-negotiable aspect of moving commercial data and system functions into the digital realm, as the potential consequences of failing to do so could be catastrophic.
However, with the right level of protection, the benefits of technological advances far outweigh the risks.

















